In the realm of digital security, JSON Web Signatures (JWS) and JSON Web Encryption (JWE) stand as fundamental tools for safeguarding data integrity and confidentiality. Both standards, defined within the JSON Web Token (JWT) suite, play crucial roles in securing data transmissions and ensuring the authenticity and privacy of information exchanged across various digital platforms.
JSON Web Signatures (JWS): Guaranteeing Data Integrity
A JSON Web Signature (JWS) serves as a digital mechanism for verifying the integrity and authenticity of a JSON object. It utilizes cryptographic algorithms to generate a signature that binds the JSON data to a specific signer, preventing unauthorized modifications or tampering. JWSs are commonly employed in applications where data integrity is paramount, such as API interactions, user authentication, and data exchange protocols.

Key Features of JWS:
Protects data integrity: Ensures that the JSON data has not been altered since it was signed.
Verifies signer identity: Confirms that the JSON data was signed by the intended signer.
Enhances data security: Prevents unauthorized access or modification of sensitive data.
JSON Web Encryption (JWE): Ensuring Data Confidentiality
JSON Web Encryption (JWE) serves as a cryptographic mechanism for protecting the confidentiality of JSON data. It utilizes encryption algorithms to transform the JSON data into an encrypted ciphertext, rendering it unreadable to unauthorized parties. JWE is particularly valuable in scenarios where data privacy is essential, such as secure messaging, sensitive data storage, and confidential data transmission.
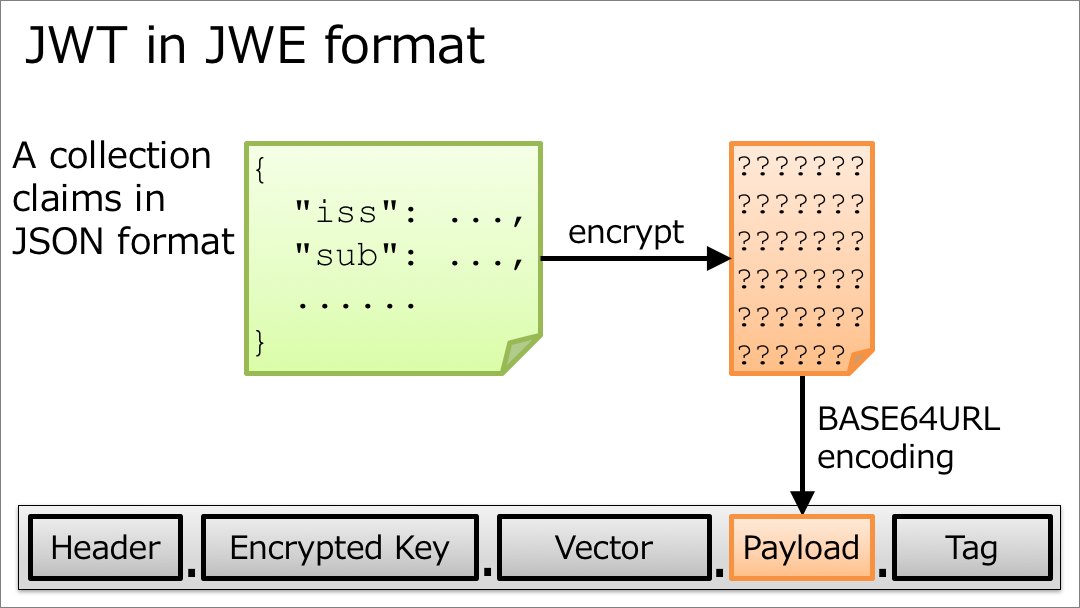
Key Features of JWE:
Protects data confidentiality: Ensures that only authorized parties can decrypt and access the JSON data.
Prevents data breaches: Safeguards sensitive data from unauthorized access and disclosure.
Enhances data privacy: Upholds the privacy of sensitive information exchanged across digital channels.
Comparing JWS and JWE: A Side-by-Side Analysis
| Feature | JWS | JWE |
|---|---|---|
| Purpose | Verifies data integrity and authenticity | Protects data confidentiality |
| Mechanism | Digital signature | Cryptographic encryption |
| Applications | API interactions, user authentication, data exchange protocols | Secure messaging, sensitive data storage, confidential data transmission |
Choosing the Right Tool: JWS vs. JWE
The choice between JWS and JWE depends on the specific security requirements of the application or data exchange scenario.
For data integrity and authenticity verification: JWS is the appropriate choice, ensuring that the data has not been tampered with and comes from a trusted source.
For data confidentiality and privacy protection: JWE is the preferred option, safeguarding sensitive data from unauthorized access and decryption.
In scenarios requiring both integrity and confidentiality: Combining JWS and JWE can provide a robust security solution, ensuring both data authenticity and encryption.
Conclusion: Securing the Digital Landscape
JWS and JWE play essential roles in modern digital security, providing mechanisms for verifying data integrity, protecting data confidentiality, and safeguarding sensitive information in the ever-evolving digital landscape. By understanding the nuances of each standard and selecting the appropriate tool for the specific application, organizations and individuals can effectively protect their data assets and maintain the privacy of their communications.